mirror of
https://github.com/microsoft/terminal.git
synced 2026-02-04 05:35:20 +00:00
Megathread: sudo, runas, mixed elevation of tabs, etc. #1381
Closed
opened 2026-01-30 22:24:14 +00:00 by claunia
·
31 comments
No Branch/Tag Specified
main
automated/loc-update
feature/llm
dev/cazamor/sui/search
dev/pabhoj/actions_editor_search
dev/lhecker/11509-kitty-keyboard-protocol
dev/lhecker/11509-kitty-keyboard-protocol-wip
dev/pabhoj/actions_editor_visual
dev/cazamor/selfhost/2026-01-29
dev/duhowett/no-blank-issues-you-lost-privileges-for-that-fam
dev/lhecker/benchcat-fix
dev/lhecker/dcs-perf
dev/duhowett/eoy-25/allow-set-foreground
release-1.24
release-1.23
dev/cazamor/bot/deprecate-area-atlasengine
dev/pabhoj/actions_editor_followups
dev/cazamor/selfhost/2026-01-20
dev/cazamor/selfhost/2026-01-12
dev/cazamor/spec/auto-save
dev/duhowett/eoy-25/underline-colors-in-atlas-bug-redux
dev/duhowett/fhl-2024/asciicast-recorder
dev/duhowett/eoy-25/underline-colors-in-atlas-bug
dev/duhowett/hax/serial-port-support
dev/duhowett/connection-utf8
dev/lhecker/fused-event
dev/lhecker/18928-wip
dev/duhowett/fhl-2024/clang
dev/cazamor/uia-leak
dev/duhowett/win7-wpf-termcontrol-squash
release-1.22
dev/cazamor/selfhost/11-18-v3
dev/cazamor/selfhost/11-18
dev/duhowett/fhl-2025/bitmap-fonts
dev/duhowett/server-2025-vms
dev/duhowett/cant-believe-gotta-do-this-shit
dev/lhecker/1410-large-scrollback
dev/lhecker/dark-mode
dev/cazamor/sui/invert-cursor-color
dev/duhowett/fhl-2025/wt-command-palette-cmdpal-integration
dev/duhowett/fhl-2025/wt-json-relative-icons
dev/lhecker/fucking-service-locator
dev/duhowett/unicode-17
dev/duhowett/multi-blern
dev/lhecker/wellp2-alt
dev/duhowett/wellp2
dev/lhecker/1860-horizontal-scrollbar
dev/lhecker/fix-window-count
dev/cazamor/sui/tab-color-old
dev/duhowett/hax/conhost-icon
dev/duhowett/hax/sui-color-chip-border
dev/duhowett/hax/terminalsettings-as-a-lib-/with-types-merged-into-tsm
dev/pabhoj/page_control_input_cleanup
dev/duhowett/padding-in-atlas-rebase-20250729
dev/lhecker/attach-thread-input
dev/duhowett/portable-shader-members
msbuildcache-reenable
dev/cazamor/selfhost/1.24-2025-06-10
dev/cazamor/upgrade-settings-containers
dev/cazamor/sui/ext-page/powershell-stub
dev/cazamor/selfhost/1.24-2025-05-15
dev/pabhoj/sui_action_overhaul
dev/cazamor/selfhost/1.24-2025-05-06
dev/cazamor/selfhost/1.24-2025-04-29
dev/cazamor/sui/ext-page/lazy-load-objects
dev/cazamor/sui/ext-page/badge
dev/cazamor/selfhost/1.24
dev/lhecker/sdk-26100
dev/duhowett/testing
dev/jadelaga/VS-Pty.Net-1.22
dev/duhowett/fhl-2025/what-if-no-content-ids
dev/cazamor/a11y/vt-seq-prototype
dev/lhecker/18584-part2
dev/lhecker/get-lang-id
dev/duhowett/hax/clogs
release-1.21
dev/pabhoj/featurellm_fix_paste
dev/lhecker/grapheme-backup
dev/jadelaga/VS-Pty.netFixes
dev/lhecker/atlas-engine-compute-shader
dev/migrie/s/ai-providers
dev/lhecker/animated-cursor-wip
dev/pabhoj/featurellm_timeout
dev/lhecker/dark-mode-alt
dev/duhowett/osc-strided-table
dev/lhecker/bugbash
dev/pabhoj/featurellm_improve_parsing
dev/duhowett/coast-to-coast
dev/lhecker/curly-improvements
dev/duhowett/net8
dev/duhowett/onebranch-custom-pool
dev/lhecker/renderer-overhaul-2nd-attempt
dev/lhecker/cleanup
dev/cazamor/sui/confirmation-announcements
dev/lhecker/theme-quality
dev/duhowett/hax/cmake
dev/lhecker/winconpty-cleanup
dev/duhowett/learn/rewrite-highlights
dev/migrie/b/no-nesting-when-searching
release-1.20
dev/lhecker/14165-conhost-font-size
dev/duhowett/sel-2-spans
dev/lhecker/7118-cursor-color
dev/lhecker/remove-glyph-width
dev/lhecker/igfw-scroll-region
dev/lhecker/17656-win32im-double-encoding
dev/duhowett/fhl-2024/merge-idls
dev/duhowett/feed-forward-variables
dev/lhecker/remove-chrome-math
dev/duhowett/copylink
dev/duhowett/applicableactions
gh-readonly-queue/main/pr-17566-de50310295b7d92ed3d51f07974a2a945776bf9d
dev/lhecker/atlas-engine-stride-copy
dev/migrie/b/bump-nuget-in-c
dev/migrie/f/992-redux-redux
dev/migrie/f/filter-weight-input-too
dev/migrie/f/disable-nesting
dev/migrie/f/local-snippets-cleaner
dev/migrie/s/1553-mouse-bindings
selfhost-1.22-bugbash-2024-06-04
selfhost/1.22-bugbash-2024-06-04
dev/lhecker/15689-tab-drag-crash-fix
dev/migrie/f/sxnui-font-size-change
dev/migrie/f/local-snippets-on-action-refactor
dev/migrie/f/just-local-snippets
dev/migrie/save-input-patches
dev/migrie/f/md-pane-official
dev/migrie/base-pane
dev/migrie/fhl/tasks-pane
release-1.19
dev/migrie/b/17130-clear-marks-2
dev/migrie/b/17075-its-me-the-killer
dev/duhowett/i-figured-out-why-sometimes-the-publish-build-failed
dev/duhowett/nuget-publication-with-aad-app-id
selfhost-1.20
dev/duhowett/graph
dev/migrie/b/15803-activate-dont-copypasta
dev/duhowett/is-pgo-broken-because-of-sui-being-slower
dev/migrie/b/remove-terminaltab
dev/migrie/fhl/md-pane
dev/migrie/fhl/local-tasks-2024
dev/migrie/fhl/2024-inline-notebook
dev/duhowett/interface-projects
dev/duhowett/dead-loc
release-1.18
dev/migrie/fhl/2024-spring-merge-base
dev/duhowett/hax/l9
inbox
dev/migrie/14073-on-main
dev/duhowett/hax/conhost_dump_replay
user/lhecker/atlas-engine-srgb
dev/migrie/fhl/sxnui-tooltips-3
dev/migrie/7718-notifications-experiments
dev/migrie/fhl/7718-notifications
dev/migrie/fhl/7718-notifications-reboot
dev/lhecker/remove-gsl
dev/lhecker/16575-TerminateProcess
dev/lhecker/window-thread-climate-control
dev/lhecker/client-context-input-output-mode
dev/lhecker/ring-buffer-input-buffer
release-1.17
dev/lhecker/propsheet-fontdlg-refactor
dev/lhecker/renderer-overhaul
dev/pabhoj/test
dev/duhowett/chop
dev/lhecker/til-ulong-cleanup
dev/lhecker/til-env-cleanup
dev/migrie/f/16005-a11y-pane
dev/cazamor/a11y/fastpass
dev/migrie/b/15487-push-cwd
dev/migrie/b/15536-or-15219-idk
dev/duhowett/move-timers-down-into-core-interactivity-etc
dev/migrie/b/15812-broadcast-paste-two
dev/migrie/fhl-fall-2023/11162-quake-III-arena
dev/migrie/fhl-fall-2023/1620-automatic-tab-progress
dev/migrie/fhl-fall-2023/9992-quake-II
dev/migrie/fhl-fall-2023/9992-default-quake-settings
dev/migrie/fhl-fall-2023/9992-window-name-settings
dev/migrie/fhl-fall-2023/oceans
dev/lhecker/ColorScheme-improvements
dev/migrie/search-v2-v3
dev/migrie/pr-15717/its-dangerous-to-go-alone
dev/migrie/f/4768-taskbar-icons
dev/duhowett/padding-in-atlas
dev/migrie/f/3121-tooltips
dev/duhowett/sticky-control
dev/duhowett/fix-tracing-2
dev/migrie/b/add-support-for-vsc-marks
dev/migrie/f/1860-this-is-literally-what-less-is-for
dev/migrie/s/5916-draft
dev/lhecker/tracy
dev/migrie/s/north-star
dev/cazamor/tag-youre-it
dev/migrie/f/12336-let-it-mellow
dev/migrie/f/now-with-more-compat-settings
dev/migrie/f/compatibility-sui
dev/duhowett/hax/wpf-atlas
dev/duhowett/fgb
dev/migrie/b/15487-relative-paths-are-hard
dev/lhecker/colrv1
loc-update
dev/migrie/fhl/dyndep-csharp
dev/migrie/fhl/dyndep
dev/migrie/fhl-clickable-send-input
dev/migrie/f/cwd-hijinks-5506-15173
dev/lhecker/openconsole-async-start
1.17
dev/migrie/bump-scratch
dev/migrie/f/3726-restartConnection
dev/migrie/b/cxn-restarting-attempt-1-backport
dev/migrie/b/9053-part-3-the-actual-doing-of-the-thing
dev/migrie/b/13388-focus-logger
dev/migrie/b/9053-part-4-i-guess-defterm
dev/migrie/oop/3/of-the-silmarils
of-the-darkening-of-valinor
dev/migrie/fhl/notebook-proto-000
dev/migrie/f/narrator-buddy
dev/migrie/mux-2.8.2-march-2023
dev/migrie/f/roast-mutton
dev/migrie/f/12861-preview-input
dev/lhecker/clang-tidy
dev/migrie/f/3121-wE-dOnT-hAvE-dEv-DaYs
dev/duhowett/compiler-compliance
dev/duhowett/i-have-a-burning-hatred-for-ntstatus-of-later-so-why-not-fix-it
dev/duhowett/shorthand-namespaces
dev/duhowett/rename-all-dlls
dev/duhowett/errordialog
dev/lhecker/gsl-narrow
dev/migrie/b/11522-dumb-idea
release-1.16
dev/miniksa/env
dev/duhowett/hax/embed-everything
dev/migrie/b/13388-attempt-003
dev/migrie/b/14512-test-research
dev/migrie/b/13388-attempt-002
dev/migrie/b/14464-copyOnSelect-moving-text
dev/migrie/s/thema-schema-for-1.16
dev/migrie/s/theme-pair-schema
dev/migrie/b/13388-experiments-1
dev/cazamor/spec/a11y-vt-seq
dev/migrie/b/14557-empty-folder-dropdown
dev/cazamor/spec/a11y-vt-seq-v2
release-1.15
dev/migrie/f/process-model-v3-test-0
dev/lhecker/vsconfig
dev/migrie/s/5000-presentation
dev/lhecker/5907-startup-perf
dev/lhecker/winrt-file-api-benchmark
dev/duhowett/128-bit-compiler
dev/duhowett/hax/arm64-native-build
dev/migrie/fhl/more-shell-integration
dev/migrie/b/13388-experiments-0
dev/lhecker/til-to-ulong-improvements
dev/migrie/s/markdown-notebooks
dev/cazamor/a11y/nav-by-page
dev/cazamor/a11y/system-menu-support
dev/duhowett/no-private-registry-keys
dev/cazamor/wpf/uia-expose-enable-events
dev/cazamor/wpf/uia-events
extendAISpec
dev/migrie/fhl/clickSendInput
dev/migrie/fhl/save-command
dev/migrie/b/theme.profile
dev/migrie/b/13943-a-test-for-this
dev/migrie/oop/2/endgame
dev/duhowett/hax/merge_idl
dev/migrie/oop/2/infinity-war
dev/migrie/spellbot-cve
dev/cazamor/a11y-sev3/new-profile-announcement
dev/migrie/fhl/upside-down-mode
release-1.14
dev/migrie/f/9458-startupInfoToTerminal
dev/migrie/fhl/5916-triggers
dev/migrie/b/13523-context-menu
dev/migrie/b/6523-endpaint-outside-lock
dev/migrie/b/12413-OnUnhandledException
dev/lhecker/render-snapshot
dev/cazamor/1.15/scroll-to-point
dev/migrie/mux-2.8-aug-2022
dev/lhecker/lock-console-guard
dev/migrie/f/1504-final
dev/pabhoj/sui_follow_ups
dev/migrie/f/til-winrt.h
dev/cazamor/color-picker-redesign
dev/migrie/fhl/vscode-autocomplete-prototype
dev/migrie/f/1504-prototype
dev/migrie/oop/2/loki
dev/migrie/oop/2/wandavision
dev/migrie/b/8698-YOURE-OUT-OF-ORDER
fabricbot-configuration-migration
dev/migrie/b/12788-did-it-work
dev/migrie/b/localtests-ci-2022
dev/cazamor/1.14/replace-compareInBounds
dev/pabhoj/preview_string
dev/cazamor/ks/switchSelectionEndpoint
dev/migrie/oop/2/COM-ISwapChainProvider-attempt-1
dev/migrie/b/dxd-marker
release-1.13
dev/migrie/b/13066-for-defterm
dev/cazamor/revert-dwm
dev/migrie/b/13066-sw_flash_repeatedly
dev/migrie/b/no-cloaky-cloak
dev/migrie/f/apples-to-oranges
dev/migrie/f/no-custom-caption-btns
dev/migrie/f/10509-mica-and-transparent-titlebars
dev/migrie/b/12911-wpf-focus-fg
dev/migrie/titebar-colors
dev/lhecker/4015-cursor
dev/migrie/fhl/rgb-rainbow-window-frame
dev/migrie/fhl/scroll-marks-prototype
release-1.12
dev/miniksa/compliance
dev/migrie/f/default-icons
dev/migrie/fhl/10175-web-search-for-text
dev/migrie/fhl/menu-complete-prototype
dev/migrie/b/2988-merged-prototypes
dev/migrie/b/2988-niksa-msgs-prototype
dev/migrie/fhl/9583-colorSelection
dev/migrie/b/10609-sui-leak
dev/migrie/b/32-attempt-3
dev/migrie/release-1.12-rejuv-attempt-2
dev/migrie/demo-for-presentation
dev/migrie/b/32-but-im-here-for-12567
dev/duhowett/conpty_first_frame_blug
dev/migrie/b/11092-unfocused-acrylic-settings
dev/migrie/localtests-in-ci
dev/migrie/b/12356-attempt-2
dev/migrie/b/12353-with-null
dev/migrie/b/12387-trim-spaces
dev/migrie/b/5033-bad-start
dev/lhecker/12351-broken-locales
dev/migrie/b/8663-input-to-oem-crash
dev/migrie/b/11743-win10-opacity-is-hard
dev/migrie/f/ctrl-click-elevate
dev/migrie/b/12196-shim-localization
dev/lhecker/issue-4015-til-rect
dev/cazamor/eim/mvvm
dev/migrie/f/--elevate
dev/migrie/b/11668-i-think
dev/migrie/b/11994-wsl-mangline
dev/migrie/eim/3475-action-xmacros
dev/migrie/eim/incremental-build-000
dev/cazamor/a11y/fake-uia-data
dev/migrie/f/non-terminal-content-elevation-warning
dev/migrie/f/632-on-warning-dialog
dev/lhecker/rgba
dev/migrie/b/8480-keybindings-in-tabs
release-1.11
dev/migrie/b/11561-dead-ends
dev/migrie/oct-21-roadmap-update
dev/migrie/fhl/adaptive-card-extension
dev/cazamor/test/11440
dev/migrie/f/warning-dlg-automation
dev/migrie/b/1.12-crash-on-exit
dev/migrie/b/11146-next-tab-in-cmdpal
release-1.10
dev/migrie/5ff9a24-and-75e2b5f
dev/duhowtt/hax/cpal-jumplist-async
dev/lelian/actionid/1
dev/migrie/f/just-elevated-state
dev/lhecker/terminal-settings-cleanup
dev/migrie/gh-10824
dev/pabhoj/cursor_light
dev/migrie/oop/wandavision
dev/migrie/oop/endgame
dev/migrie/oop/infinity-war
dev/lhecker/app-state-actually-hidden
dev/migrie/b/6160-dynamic-default-warning
dev/mgirie/b/more-nchhittest-ideas
dev/migrie/b/9320-interfacial-separation
cinnamon/fhl/find-contextmenu
dev/lhecker/wsl-distro-generator-cleanup
dev/migrie/b/10875-but-more-clever
dev/migrie/b/broken-globalsummon-overloading
dev/duhowett/hax/rle-row
dev/migrie/fhl-2021/cmdpal-select-list
dev/migrie/fhl-2021/differential-pixel-shading
dev/duhowett/hax/no-writable-glyphat
dev/migrie/fhl-2021/more-shader-variables
dev/migrie/titlebar-shenannigans
dev/miniksa/win10_font_matching
dev/lhecker/conhost-oom
dev/migrie/b/10332-less-snappy-scrolling
dev/migrie/b/7422-1px-top-border
release-1.9
dev/cazamor/move-scratch
release-1.8
dev/miniksa/manifest_2
release-1.6
release-1.7
dev/migrie/oop/the-whole-thing
dev/migrie/oop/connection-factory
dev/migrie/f/quake-dropdown-2
dev/miniksa/rle2
dev/migrie/f/quake-toCurrent-experiments-2
dev/migrie/f/quake-toCurrent-experiments
dev/migrie/f/quake-dropdown
dev/cazamor/actions-page/template
dev/duhowett/hax/cursor_stamp_foreground_background
dev/migrie/f/1860-hey-might-was-well-hack-during-a-hackathon
dev/migrie/oop-terminal.control-split-control
dev/duhowett/hax/build-with-wholearchive
dev/cazamor/spec/tsm-actions-temp
dev/migrie/oop-tear-apart-control
dev/migrie/oop-scratch-3
dev/cazamor/sui/bugfix-reload-crash
dev/migrie/f/xmacro
dev/cazamor/sui/proto/profile-nav-view
dev/migrie/f/name-windows
dev/migrie/dol/messing-with-shaders-take-1
release-1.5
dev/cazamor/sui/inheritance-hyperlinks-test
dev/migrie/r/commandline-lib-002
dev/migrie/f/com.fabrikam.toaster
dev/cazamor/adaptive-cards-prototype
dev/migrie/f/commandline-lib
dev/miniksa/zipzoom2
dev/migrie/f/remote-commandlines
dev/migrie/f/632-elevated-profiles
dev/migrie/oop-broker-000
dev/migrie/fix-pr-7015
dev/duhowett/clang
dev/miniksa/input_tests_2
dev/miniksa/input2
dev/migrie/oop-rpc-000
release-1.4
dev/migrie/oop-mixed-elevation-1
dev/migrie/oop-window-content-1
cinnamon/open-json
dev/miniksa/input_tests
dev/duhowett/hax/tsm-graphviz
dev/miniksa/input
dev/duhowett/hax/caption_buttons
release-1.3
dev/cazamor/a11y/expand-line-under-viewport
dev/cazamor/acc/ch/word-nav-perf
dev/cazamor/spec/settings-ui-architecture-draft
dev/duhowett/hax/tap_upgrade
dev/migrie/f/pane-exit-animation
release-1.2
dev/migrie/move-lib-up-and-dll-down
release-1.1
dev/migrie/f/branch-2-backup
dev/migrie/f/settings-getters-only
dev/duhowett/hax/command_palette_search
dev/migrie/f/6856-let-terminalpage-expandcommands
dev/migrie/f/theming-2020
dev/migrie/oop-scratch-4
dev/duhowett/hax/punchout
dev/migrie/s/action-ids
dev/migrie/f/lets-just-generate-these
dev/migrie/oop-scratch-2
dev/miniksa/dcomp
dev/miniksa/gotta_go_fast_spsc
dev/miniksa/gotta_go_fast
dev/miniksa/perf_skip_checks
dev/miniksa/perf_buffer_dig
dev/migrie/s/1203-cursorTextColor
dev/migrie/f/fix-intellisense-i-guess-backup
release-1.0
dev/migrie/f/execute-commandlines
dev/migrie/f/2046-Command-Palette-v2
dev/migrie/b/6421-passthrough-alt
dev/migrie/b/moving-focus-is-hard
dev/miniksa/set
dev/migrie/f/1203-phase-1
dev/migrie/f/get-localtests-in-ci
dev/cazamor/drag-panes
dev/cazamor/tile-background
release-0.11
dev/duhowett/dev/duhowett/hax/appstate_remember
dev/duhowett/load_condrv
dev/duhowett/hax/wpf_win_8_hax
dev/migrie/b/3088-weird-exact-wrap-resize
release-0.10
dev/migrie/b/4591-custom-scaling-bug
dev/duhowett/hax/attr_smuggling
dev/migrie/b/5161-mingw-vim-fix
dev/miniksa/dx_bitmap
dev/migrie/b/1503-try-messing-with-cooked-read
dev/duhowett/eyebeam
dev/migrie/b/5113-experiments
dev/duhowett/hax-selection-exclusive
dev/migrie/f/more-vt-renderer-tracing
dev/miniksa/bitmap
dev/duhowett/wprp
dev/miniksa/bitmap-mad-with-power
dev/migrie/f/resize-quirk
dev/migrie/f/reflow-buffer-on-resize-002
wpf-renderer-revert
dev/miniksa/draw
release-0.9
dev/miniksa/tabs-color-fix
dev/miniksa/4309
dev/migrie/f/just-wrapping
dev/migrie/b/3490-try-another-resize-algo
release-0.8
dev/migrie/b/3490-a-simpler-resize
dev/migrie/b/3490-resize-down
dev/miniksa/4254
dev/migrie/f/conpty-wrapped-lines-2
dev/migrie/b/be-better-at-hiding
dev/migrie/f/3327-xaml-theming-proto
dev/miniksa/gardening2
release-0.7
dev/duhowett/conpty-flags
dev/migrie/f/603-vintage-opacity
dev/migrie/PR#3181-comments
dev/duhowett/font-64
release-0.5
dev/migrie/b/663-paste-lf-always
dev/migrie/b/2011-reordered-fallthrough-strings
dev/migrie/b/411-init-tab-stops
dev/migrie/b/json-patching-is-hard
dev/migrie/b/2455-try-getting-tests-working
dev/migrie/b/1223-change-256-table
dev/migrie/f/2171-openterm.cmd
dev/migrie/f/drag-panes
dev/migrie/f/2046-command-palette
release-0.3
dev/miniksa/manager
dev/migrie/f/non-terminal-panes
dev/migrie/f/passthrough-2019
dev/miniksa/shared_pch
dev/migrie/f/1897-less-duplicated-work
release-0.2
dev/cazamor/mcs/viewport-selection
dev/duhowett/version_hack
v1.24.10212.0
v1.23.20211.0
v1.24.3504.0
v1.23.13503.0
v1.24.2812.0
v1.23.12811.0
v1.24.2682.0
v1.23.12681.0
v1.24.2372.0
v1.23.12371.0
v1.23.12102.0
v1.22.12111.0
v1.23.11752.0
v1.22.11751.0
v1.22.11141.0
v1.23.11132.0
v1.23.10732.0
v1.22.10731.0
v1.21.10351.0
v1.22.10352.0
v1.23.10353.0
v1.22.3232.0
v1.21.3231.0
v1.22.2912.0
v1.21.2911.0
v1.22.2702.0
v1.21.2701.0
v1.22.2362.0
v1.21.2361.0
v1.21.1772.0
v1.20.11781.0
v1.21.1382.0
v1.20.11381.0
v1.21.1272.0
v1.20.11271.0
v1.20.11215.0
v1.19.11213.0
v1.20.10822.0
v1.19.10821.0
v1.20.10572.0
v1.19.10573.0
v1.20.10303.0
v1.19.10302.0
v1.18.10301.0
v1.20.10293.0
v1.19.10292.0
v1.18.10291.0
v1.18.3181.0
v1.19.3172.0
v1.19.2831.0
v1.18.2822.0
v1.19.2682.0
v1.18.2681.0
v1.18.1462.0
v1.17.11461.0
v1.18.1421.0
v1.17.11391.0
v1.17.11043.0
v1.16.10261.0
v1.17.1023
v1.16.10231.0
v1.15.3465.0
v1.16.3463.0
v1.15.2712.0
v1.15.2874.0
v1.16.2641.0
v1.16.2523.0
v1.15.2524.0
v1.15.2282.0
v1.14.2281.0
v1.14.1962.0
v1.15.2002.0
v1.15.2001.0
v1.15.1862.0
v1.14.1861.0
v1.14.1451.0
v1.14.1432.0
v1.13.11431.0
v1.13.10983.0
v1.12.10982.0
v1.13.10733.0
v1.12.10732.0
v1.13.10395.0
v1.12.10393.0
v1.13.10336.0
v1.12.10334.0
v1.12.3472.0
v1.11.3471.0
v1.12.2931.0
v1.12.2922.0
v1.11.2921.0
v1.11.2731.0
v1.10.2714.0
v1.11.2421.0
v1.10.2383.0
v1.10.1933.0
v1.9.1942.0
v1.9.1523.0
v1.8.1521.0
v1.9.1445.0
v1.8.1444.0
v1.8.1092.0
v1.7.1091.0
v1.8.1032.0
v1.7.1033.0
v1.7.572.0
v1.6.10571.0
v1.5.10411.0
v1.6.10412.0
v1.6.10272.0
v1.5.10271.0
v1.5.3242.0
v1.4.3243.0
v1.5.3142.0
v1.4.3141.0
v1.4.2652.0
v1.3.2651.0
v1.3.2382.0
v1.2.2381.0
v1.1.2233.0
v1.2.2234.0
v1.1.2021.0
v1.2.2022.0
v1.1.1812.0
v1.0.1811.0
v1.1.1671.0
v1.0.1401.0
v0.11.1333.0
v0.11.1251.0
v0.11.1191.0
v0.11.1111.0
v0.11.1121.0
v0.10.781.0
v0.10.761.0
v0.9.433.0
v0.8.10261.0
v0.8.10091.0
v0.7.3451.0
v0.7.3382.0
v0.7.3291.0
v0.7.3252.0
v0.6.3181.0
v0.6.2951.0
v0.6.2911.0
v0.5.2762.0
v0.5.2761.0
v0.5.2681.0
v0.5.2661.0
v0.3.2321.0
v0.4.2342.0
v0.4.2382.0
v0.3.2171.0
v0.3.2142.0
v0.2.1831.0
v0.2.1715.0
v0.2.1703.0
v0.1.1621.0
v0.1.1581.0
v0.1.1502.0
v0.1.1431.0
v0.1.1361.0
v0.1.1093.0
v0.1.1161.0
v0.1.1204.0
experiment-master
v0.1.1025.0
experiment-OutsideBuild
broken-tabstops
RS2-final
v0.1.1002.0
experiment-rel-windows-inbox
experiment-f-ServerApp
v0.1.1211.0
1904.29002
1810.02002
1708.14008
Labels
Clear labels
⛺ Reserved
A11yCO
A11yMAS
A11ySev1
A11ySev2
A11ySev3
A11yTTValidated
A11yUsable
A11yVoiceAccess
A11yWCAG
Area-Accessibility
Area-AtlasEngine
Area-AzureShell
Area-Build
Area-Build
Area-Chat
Area-CmdPal
Area-CodeHealth
Area-Commandline
Area-CookedRead
Area-DefApp
Area-Extensibility
Area-Fonts
Area-GroupPolicy
Area-i18n
Area-Input
Area-Interaction
Area-Interop
Area-Localization
Area-Output
Area-Performance
Area-Portable
Area-Quality
Area-Remoting
Area-Rendering
Area-Schema
Area-Server
Area-Settings
Area-SettingsUI
Area-ShellExtension
Area-ShellExtension
Area-ShellExtension
Area-Suggestions
Area-Suggestions
Area-TerminalConnection
Area-TerminalControl
Area-Theming
Area-UserInterface
Area-VT
Area-Windowing
Area-WPFControl
AutoMerge
Blocking-Ingestion
Culprit-Centennial
Culprit-WinUI
Disability-All
Disability-Blind
Disability-LowVision
Disability-Mobility
External-Blocked-WinUI3
Fixed
Gathering-Data
good first issue
HCL-E+D
HCL-WindowsTerminal
Help Wanted
Impact-Compatibility
Impact-Compliance
Impact-Correctness
Impact-Visual
In-PR
InclusionBacklog
InclusionBacklog-Windows TerminalWin32
InclusionCommitted-202206
Issue-Bug
Issue-Docs
Issue-Feature
Issue-Feature
Issue-Question
Issue-Samples
Issue-Scenario
Issue-Task
Needs-Attention
Needs-Author-Feedback
Needs-Bisect
Needs-Discussion
Needs-Repro
Needs-Tag-Fix
Needs-Tag-Fix
Needs-Triage
No-Recent-Activity
Priority-0
Priority-1
Priority-2
Priority-3
Product-Cmd.exe
Product-Colortool
Product-Colortool
Product-Colortool
Product-Conhost
Product-Conpty
Product-Meta
Product-Powershell
Product-Terminal
Product-WSL
pull-request
Resolution-Answered
Resolution-By-Design
Resolution-Duplicate
Resolution-External
Resolution-Fix-Available
Resolution-Fix-Committed
Resolution-No-Repro
Resolution-Won't-Fix
Severity-Blocking
Severity-Crash
Severity-DataLoss
spam
this-will-be-a-breaking-change
Tracking-External
WindowsTerminal_Win32
Work-Item
zAskModeBug
zInbox-Bug
Mirrored from GitHub Pull Request
Milestone
No items
No Milestone
Projects
Clear projects
No project
Notifications
Due Date
No due date set.
Dependencies
No dependencies set.
Reference: starred/terminal#1381
Reference in New Issue
Block a user
Blocking a user prevents them from interacting with repositories, such as opening or commenting on pull requests or issues. Learn more about blocking a user.
Delete Branch "%!s()"
Deleting a branch is permanent. Although the deleted branch may continue to exist for a short time before it actually gets removed, it CANNOT be undone in most cases. Continue?
Originally created by @hansmbakker on GitHub (May 27, 2019).
Summary of the new feature/enhancement
Current situation:
Currently most console apps (Powershell, CMD) need to start a new session for getting administrator access. This results in a less optimal workflow, because then you lose
cdinto it again)Proposed technical implementation details (optional)
A bit like
sudo, started with a button:@oising commented on GitHub (May 27, 2019):
@hansmbakker Windows Terminal (or any terminal for that matter) doesn't - and cannot - know anything about sessions, command history, or locations. It's just a (virtual) screen and a (virtual) keyboard that connects to whatever client (cmd, powershell, bash) the user wants to use. The responsibility for managing that information lies with the clients (applications) themselves. I understand what you're asking, and sympathize though. Using
sudoin linux/osx makes life a bit easier at the command line, but unfortunately this isn't the way the Windows operating system is structured. Admin (elevated) processes and regular or restricted processes cannot communicate with each other. If you want something running as administrator, a new process is required.Thanks for your feedback, but I'm going to close this as it's not feasible in the manner you would like.
@mdtauk commented on GitHub (May 27, 2019):
Couldn't each tab run in it's own isolated process - with some being elevated, and others not - but in the same Window?
@oising commented on GitHub (May 27, 2019):
@mdtauk In theory, yes. But (1) this isn't what the op is asking, and (2) I'm not certain if ConPTY is baked enough to allow this yet. At a minimum, I'd imagine the main terminal process would need to be elevated, or at least some kind of proxy process would need to be, but that means we'd then have to create a means of communication between the terminal, the proxy (which is a conpty server) and the elevated app (conpty client.) Things get hairy fast after that.
@mdtauk commented on GitHub (May 27, 2019):
@oising Thanks for the reply. I think this suggestion has cropped up previously, and was wondering of the feasibility.
Its not as elegant as typing sudo or even elevate. But adding a profile for an elevated prompt which when clicked/tapped - brings up the UAC dialog, and then creates the elevated tab within the window - could be useful.
@hansmbakker commented on GitHub (May 27, 2019):
It's a pity that it is unfeasible, but thank you for your explanation.
@DHowett-MSFT commented on GitHub (May 27, 2019):
Hosting a connection to an elevated process in a window owned by a medium-integrity (that is: not elevated) process is dangerous because any other medium-integrity process could possibly inject input into it or scrape output from it. That’s the sole reason we’ve been given by the windows security team to not endeavour to do this.
@hansmbakker commented on GitHub (May 27, 2019):
Thanks for being transparent about it.
On the technical side, I’m wondering why
sudoworks while what I asked for can cause risks?@mdtauk commented on GitHub (May 27, 2019):
Sudo is a Linux concept, and the way User and Admin concepts are handled between Linux and Windows are very different, and I guess that is what makes it not possible.
@sedwards2009 commented on GitHub (May 28, 2019):
Anytime someone uses
sudoinside a terminal running on their normal Windows account, that scenario happens. It is extremely common. Linux users/admins do it all the time. My web browser also has access to mega-tons of sensitive data and accounts which I care about, but the browser itself is also just a normal process subject to the attack described above.I'm not really familiar with the Windows security model and what is possible, but is it an idea for the terminal process to run protected from injection and scraping by default?
@zadjii-msft commented on GitHub (May 28, 2019):
@DHowett-MSFT do we have a sudo megathread that combines all the 100 ways we've said no? Because we really should at this point
@zadjii-msft commented on GitHub (May 29, 2019):
Congratulations, this is the sudo megathread now. (I liked this number the most of all the issues that currently existed.)
Real quick linking all the other issues I can find that are related:
#691 #632 #146
@thomassth commented on GitHub (Jun 24, 2019):
Please re-open this thread as I think this is a solvable problem, not an impossibility.
Copying from another thread, since I see no one object this idea yet:
"Open Terminal as Admin" at the dropdown list
@glennsarti commented on GitHub (Jul 1, 2019):
@thomassth
Disclaimer - I am not a developer etc. on the terminal project, just a user. And my knowledge of UWP is cursory at best.
Trying to add a " ... as a administrator" shortcut is unfortunately going to be difficult because the Windows Terminal application is not a "traditional" win32 app (like PowerShell or cmd.exe), it's packaged as a UWP application. And UWP is specifically does not allow this. For example
EDIT - Terminal isn't UWP, it's packaged as a UWP.
Ref - https://docs.microsoft.com/en-au/windows/msix/desktop/desktop-to-uwp-prepare
Ref - https://docs.microsoft.com/en-us/windows/uwp/packaging/app-capability-declarations
HOWEVER all hope is not lost. UWPs can't just be started from the commandline, for example running
C:\Program Files\WindowsApps\Microsoft.WindowsTerminal_0.2.1715.0_x64__8wekyb3d8bbwe\WindowsTerminal.exefrom the command line will result in an "Access Denied"But you CAN start them via the APX Activation Manager. This gist
https://gist.github.com/ridomin/e222147e7b6891e5df086cce6b5dc218#file-startuwpfromcommandline-ps1-L150-L165
Shows a powershell way to run an arbitrary UWP app. So you could run
Start-Locally -ID Microsoft.WindowsTerminalFROM an already elevated process (or say, a contrived shortcut) run the parent process in an elevated context.@DHowett-MSFT commented on GitHub (Jul 1, 2019):
@glennsarti you’re partially right. The terminal isn’t a UWP, but it is MSIX-packaged like one. Because it’s not a UWP, though, you can just use “Run as administrator” on it. The thing it doesn’t, and probably cannot safely (per discussion above) support is running processes from multiple integrity levels in the same session.
@glennsarti commented on GitHub (Jul 1, 2019):
Thanks @DHowett-MSFT ! (Yeah, my UWP isn't the best 😞 ) I've edited my original comment. One thing's that odd though. I can't save that I want to always elevate. I'm putting this down to UWP because the "Target type" isn't
Applicationbut the qualified APPX ID...I added a "Standard" shortcut for comparison in the screenshot.
Yup 100% agree.
@chucker commented on GitHub (Jul 1, 2019):
Is there no facility for a cross-process framebuffer (like macOS's IOSurface, and perhaps like Chromium's architecture)? Or is the problem that such processes must be from the same login session?
@SHDMBelangerAlexandre commented on GitHub (Jul 3, 2019):
What I did to make as admin to work, I logged as my admin user, downloaded the App from the store and it was working. But I have other issue when there is an update. Not really the best way to do it imho.
@mdtauk commented on GitHub (Jul 16, 2019):
Perhaps it should be treated in the same way as an "InPrivate" tab?
@alefranz commented on GitHub (Aug 23, 2019):
I have a maybe related question.
Would hosting a process of a powershell running on a remote machine through RemoteApp not be feasible for similar reason?
@yllekz commented on GitHub (Nov 15, 2019):
Could Windows Terminal instead treat the tabs as individual processes running as whatever user you choose? The host WindowsTerminal.exe could run as the current user but the tabs could have options to run as a separate user.
Honestly the lack of this feature will probably make or break my decision to even use this because I have a need to run PS as different users to properly secure environments and fulfill RBACs.
@gerardog commented on GitHub (Jan 16, 2020):
For the brave, let me introduce you a workaround based on
gsudo, my open-sourcesudo for windowsimplementation. (MIT License)Install gsudo, then add a new profile to Windows Terminal:
This allows Windows Terminal to mix elevated and non-elevated consoles. Also, you can use
gsudoto elevate simple commands from a non-elevated console.gsudohas an experimental ConPty mode, not enabled by default (usegsudo --vt [command]) that works pretty much that way. It spans the elevated process in a PseudoConsole and streams VT sequences to the non-elevated console.According to that criteria, is it safe to
ssh root@otherserverfrom a non elevated console? Other non-elevated process could also inject or scrape ssh or the console.Anyway, I've read this advice seriously and while I've already taken all security meassures that I could think of, I am totally open to criticism, advice, suggestions or bug reports.
EDIT: looks like
linux sudohas always beenvulnerablein this way. (I've only tested using WSL)@ossdesign commented on GitHub (Apr 4, 2020):
@gerardog Thanks for sharing the "gsudo" workaround (and for putting it together!!) I gave it a try, and it works well enough for my needs at this point. I don't know enough about how the security stuff works to know how big off on an issue it is to launch a new tab like this.
I have historically (and still do) use ConsoleZ, which really is a just a "wrapper" to launch hidden (launched off-screen at some large negative (-XXXXX, -XXXXX) coordinates, and then does some trickery with what is available to read and write to it (I have read there is screen scraping involved to read, but do not know the details.) This being the case, I assume each tab really is just interacting with its own Cmd, PowerShell, whatever process. I assume ConEmu and others do something similar.
I guess the question is, it sounds like Windows Terminal does not just wrap other processes. I know knowing about the evolving low-level Windows plumbing involved with this, so I don't know the issues involved. And I don't know for sure what the security concerns may be using "gsudo" as you outline above. For my usage cases, it gives me a quick elevated Cmd (or PowerShell) tab to get something, and then get out. Either way, thanks!
@grave0x commented on GitHub (May 1, 2020):
would something like this work? https://github.com/lukesampson/psutils/blob/master/sudo.ps1
tho i have no idea how you'd run it without Powershell
@matthew4850 commented on GitHub (Jun 22, 2020):
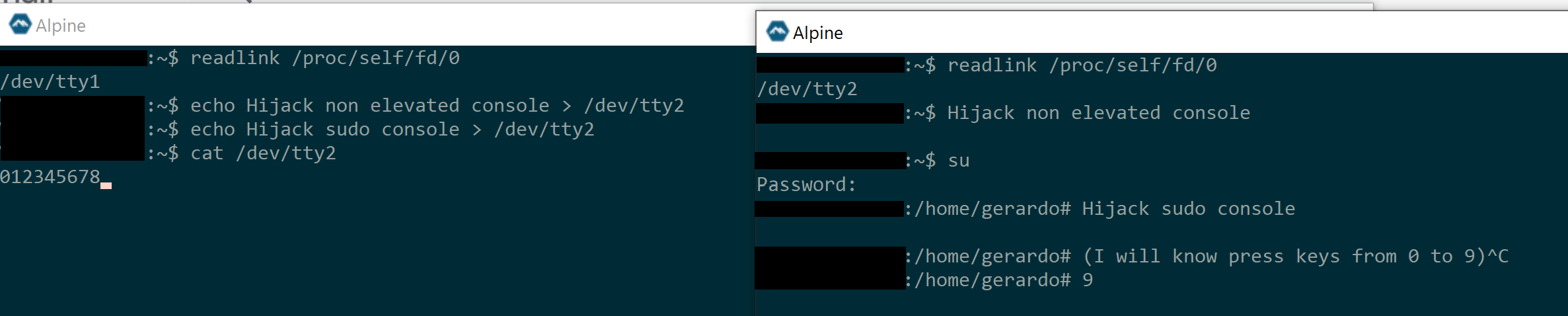
When you do
echo test > /dev/tty2it first runs the echo command and then writes its output to/dev/tty2so while it is possible for a lesser privileged process to write to attyused by a high privileged process, it is not possible for the lesser privileged process to run a command with higher privileges.@DHowett commented on GitHub (Jun 22, 2020):
I'm more concerned about whatever X11 allows than "i can write to a tty device" (which only impacts the output stream)
@darealshinji commented on GitHub (Feb 14, 2021):
@glennsarti:
Create a fresh shortcut (right click desktop -> new shortcut) and enter
wt.exeas the target. That will allow you enable "Run as Administrator". You can find an icon to use here in the directoryres@sylveon commented on GitHub (May 28, 2021):
Random thought: wouldn't it be possible, in Windows, to allow unelevated app to opt-in to UIPI (via the app manifest, for example) so that they are effectively isolated like admin apps, while still not actually running as admin?
That would resolve the scraping/injection concern, opening up the possibility to run mixed tabs elevation.
@zadjii-msft commented on GitHub (May 28, 2021):
@sylveon That's maybe possible, though I don't know about that too much. Would that break screen readers or other accessibility tools? Or even IMEs? I'd love to see a proof-of-concept!
@sylveon commented on GitHub (May 28, 2021):
Screen readers, IMEs and other accessibility tools already use UI Access to punch a hole in UIPI, so there shouldn't be much of an issue here.
However I can't come up with a PoC because it would require platform support (afaik) and I'm not a Windows developer yet ;)
@zadjii-msft commented on GitHub (May 28, 2021):
Huh. Shame I'm on leave for the next month, otherwise I'd give it a go. Maybe when I get back...
Oh wait, nevermind. That's why this won't work:
so the problem here is
OH I see - you're suggesting that we modify UIPI to enable this scenario, rather than "this is something that you can do as an app developer today". Okay. That makes more sense. I'm all over the place today. Sorry for the confusion.
@sylveon commented on GitHub (May 28, 2021):
Indeed, I was suggesting modifying UIPI in the OS itself to support this scenario: blocking the communication between malicious.exe and wt.exe even at the same (or lower) IL